Amid the craze for Arbitrum airdrops, what do you think of the anti-Wycrime mechanism?
Original title: "In-depth | How do you view the anti-witch mechanism under the craze of Arbitrum airdrops?"
Original author: Beosin
Recently, the Ethereum Layer 2 extension protocol Arbitrum airdrop has become a hot topic in the cryptocurrency community.
On-chain data shows that Arbitrum's number of transactions on March 22 exceeded 1.21 million, a record high, while exceeding the 1.08 million transactions of the Ethereum mainnet and Optimism's 260,000 transactions. Its popularity can be seen.
Arbitrum is a Layer 2 extension protocol with high performance, low cost and decentralization. After the airdrop on the evening of March 16, a large number of "fleecing" users were restricted by a series of anti-witch rules. Today, let's study what anti-witch rules are.

Speaking of Sybil attacks, many of you should be familiar with them. In blockchain, Sybil attacks refer to attacks in which attackers forge multiple identities or nodes to control the network.
Airdrop Sybil Attack is an attack method against cryptocurrency airdrop activities, in which attackers use forged identities and fake addresses to obtain more airdrop tokens.
To talk about anti-Sybil rules, let's start with the rules of this airdrop.
Arbitrum Airdrop Rules and Detection Model
In the Arbitrum token airdrop, some airdrop strategies and allocation models were developed to ensure in a quantitative way whether each wallet or on-chain entity address meets the airdrop qualification criteria:
1. If all transactions of the airdrop recipient's wallet occur within 48 hours, 1 point will be subtracted.
2. If the airdrop recipient's wallet balance is less than 0.005 ETH and the wallet does not interact with more than one smart contract, one point will be subtracted.
3. If the wallet address of the airdrop recipient is identified as a Sybil address during the Hop Protocol Bounty Program, the recipient will be disqualified.
4. There is also a standard that the project party has not confirmed, that is, if a user connects to multiple wallets with the same IP on http://arbitrum.foundation, he will be directly disqualified from the list.

At the same time, Arbitrum uses on-chain data to identify related addresses owned by the same user, and uses data from Nansen, Hop, and OffChain Labs to remove entity addresses such as bridges, exchanges, and smart contracts. Some addresses are also removed through manual inspection, such as donation addresses.
The following data types are used for data cleaning:
1. Original qualification list address (from Nansen)
2. Excluded entity address (from Nansen)
3. CEX deposit address (from Nansen)
4. CEX deposit address (traced back to CEX’s hot wallet)
5. Transaction routes unique to the Arbitrum chain (from, to)
6. Transaction routes unique to the Ethereum chain (from, to)
7. OffChain Labs’ internal address list
8. Blacklist in the Hop airdrop
9. Addresses after the Sybil attack is removed in the Hop airdrop
10. Nansen address tags
11. Other manually marked active addresses
After data cleaning, two types of charts will be generated.
The first type of graph will have one edge (from_address, to_address) for each transaction with msg.value.
The second type of graph will have one edge (from_address, to_address) for each funder/sweep transaction, where a funder transaction is the first ether deposited to an account and a sweep transaction is the last ether transferred from an account.
Clusters are generated by partitioning the above graph into strongly connected and weakly connected subgraphs. Use the Louvain community detection algorithm to decompose large subgraphs, providing more refined results and more accurate elimination of Sybil addresses.
Sybil clusters are identified based on known patterns, such as: addresses with similar activity transferred in clusters of 20+ addresses funded by the same source
This generated Sybil clusters as follows:
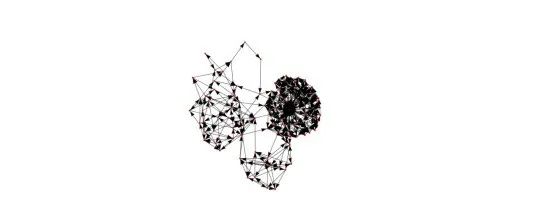
Cluster 319 containing 110 Sybil attack-eligible addresses
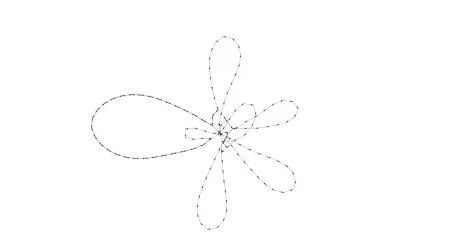
Cluster 1544 containing 56 Sybil attack-eligible addresses
How did researchers identify Sybil addresses?
Offchain Labs researchers identified possible Sybil wallets by using a clustering algorithm on from_address/to_address transaction data from Nansen Query and integrating tracking and token transfers on Arbitrum and Ethereum, and manually "checked" the data for possible false positives.
The following figure is an example of a suspected Sybil address: Among a group of about 400 addresses, two addresses have very similar activities (sending funds to the same centralized exchange deposit address).
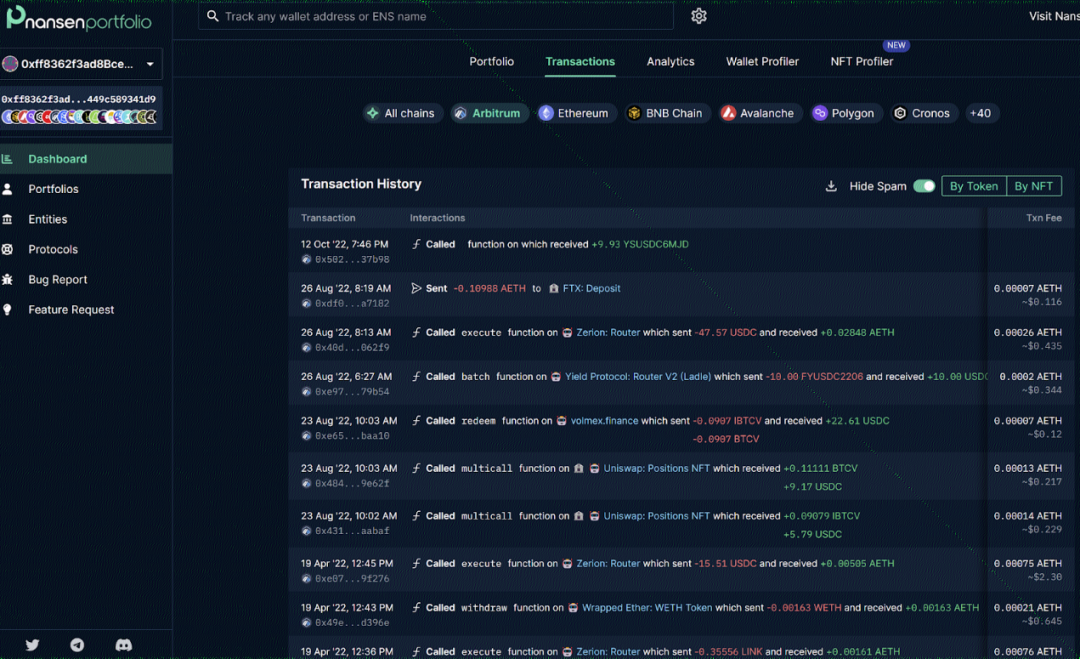
Image source nansen
You can see that the two addresses performed similar operations at very close times.
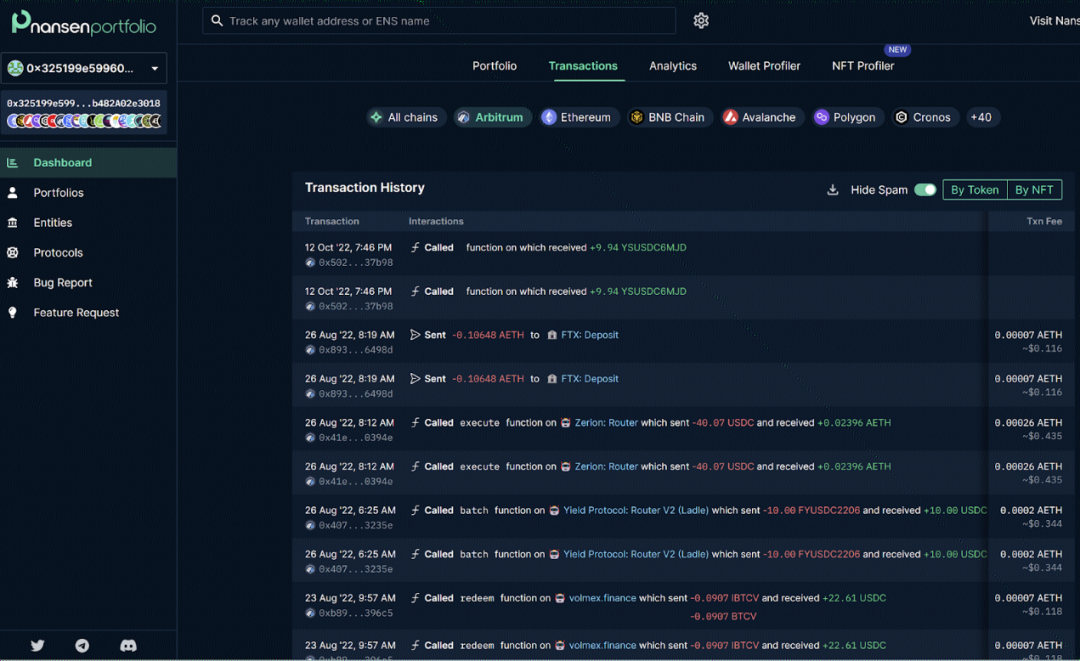 Image source nansen
Image source nansen
Of course, despite this, some people still complain about the flaws in Arbitrum's airdrop strategy, treating the wallet addresses of Sybil attacks as normal, while the wallet addresses of real users are restricted.
In addition to the recent Arbitrum, a large number of Sybil attackers were also identified through anti-Sybil rules during the Hop Protocol airdrop last year.
Sybil attackers during the Hop Protocol airdrop
On May 6, 2022, the cross-chain bridge Hop Protocol officially announced the airdrop details and stated that 10,253 of the 43,058 addresses that initially met the airdrop conditions were identified as Sybil attackers.
The following are some of the criteria used by the Hop Protocol project to determine a Sybil attack:
1. Multiple addresses have a unified fund distribution or collection address, proving that it was initiated by a Sybil attacker, such as:
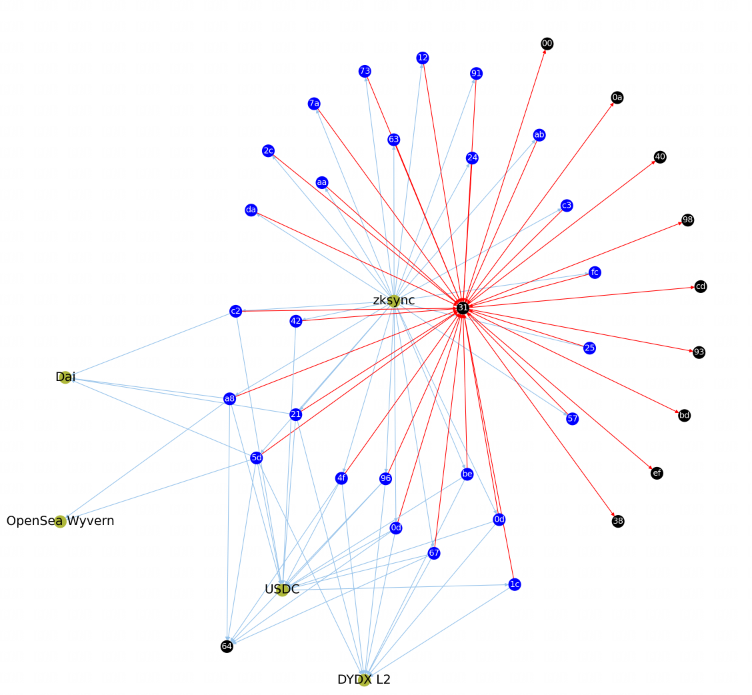
Source: Sybil Attacker Report #275
2. Multiple addresses have obvious correlations in transfer records, such as:
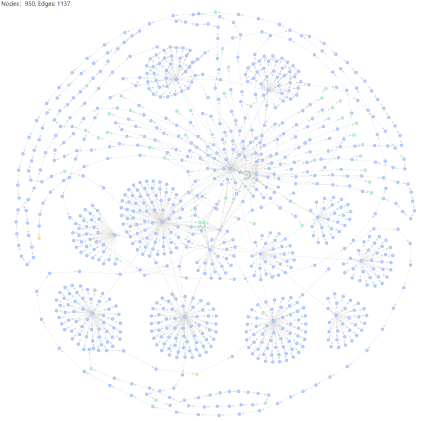
Source: Sybil Attacker Report #367
3. There are traces of batch operations in multiple places of a Sybil attack, including but not limited to: batch transfers in a short period of time, gas value The same, similar interaction amounts, etc.
4. The interaction history of the witch address has attack records of other projects in the past.
Of course, there are also inexperienced project parties who did not formulate anti-witch rules when opening airdrops, such as Aptos.
Looking back at Aptos's anti-conventional airdrop, did the wool party win?
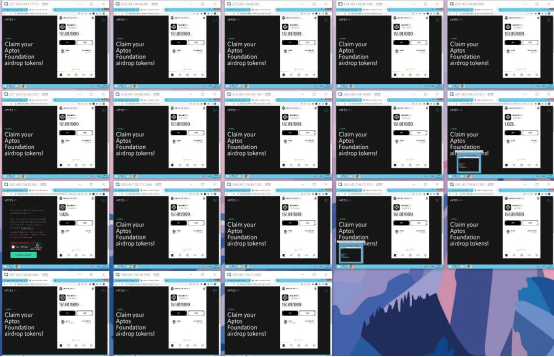
In the Aptos airdrop event last October, because the project party did not prevent witch attacks on the nodes, many "wool party scientists" received a large number of airdrops. Someone shared a screenshot of his application for the Aptos test network on Twitter and the community, and you can see the application interface of multiple trumpets on the VPS host. According to feedback from community users who applied for tokens, the airdrop rule of Aptos is that each account applying for the test network can get 300 tokens, and users who cast NFTs have 150 tokens. So if you have 100 accounts, you can get 30,000 tokens, and 1,000 accounts, you can get 300,000 tokens.

Screenshots of community users claiming airdrops
After Aptos was launched on Binance, the price instantly stretched, and then there was a huge market crash. According to the analysis of researchers, among the Aptos addresses deposited to Binance at that time, Sybil attack addresses accounted for 40%. It can be seen that the airdrop Sybil attack will have a certain impact on both the airdrop project and the participants, such as the token price being affected, the reputation of the airdrop plan being damaged, and the community builders and participants being affected.
How to formulate anti-sybil attack rules?
When airdropping, the airdrop project party will use the anti-sybil mechanism to prevent malicious users from obtaining too many tokens through multiple wallet addresses or other means, thereby distributing tokens to real users.
From past airdrop events, we can see the characteristics of Sybil attacks:
1. Sub-addresses distribute/collect funds from the same parent address
2. Exactly the same interaction process, time and project
3. Same GAS value, transaction amount and time
4. Frequent transfers between addresses.
Below are some anti-sybil mechanisms that airdrop project parties may use.
Snapshot time:Airdrop project parties can take a snapshot of all addresses at a specific time point and airdrop tokens to addresses that already hold tokens before that time point. This prevents malicious users from creating new addresses after the snapshot time to obtain tokens.
Interaction route:Take the addresses that interact with this project within a period of time, and check the consistency of the interaction paths of these addresses before/after participating in the interaction with this project according to the interaction time.
Fund flow:Mainly check the flow direction of funds, and check the one-to-many or many-to-one transfer of wallets.
Interaction amount:Check the size of the project interaction quota and the reuse rate of funds.
Interaction frequency:Export the details of the addresses that interact with the project within a certain period of time, and use Excel pivot charts or the project's self-developed dashboard to take the data within the abnormal peak period for secondary research. You can check whether the activity level of this batch of addresses is similar.
Interaction depth:Take the details of the addresses that participated in the interaction with this project within a certain period of time. Check whether the number of interactions in the past and after participating in the interaction with this project are sufficient.
Proof of Stake:Proof of Stake (PoS) is a consensus mechanism used by some blockchains to validate transactions. In PoS, users need to hold a certain number of tokens to participate in the network. Airdrop projects can require participants to hold a certain number of tokens to be eligible for airdrops, raising the threshold for airdrops.
KYC/AML Verification:Airdrop projects can require participants to pass a KYC (know your customer) or AML (anti-money laundering) verification process. This process can help verify the identity of participants, which helps prevent Sybil attacks.
Social Media Verification:Airdrop projects can require participants to follow, like, or retweet social media posts to qualify for airdrops. This helps ensure that participants are real people and not automated scripts.
Whitelist:A whitelist is a list of addresses that are eligible for airdrops. Airdrop projects can limit airdrops to a pre-approved list of participants, which helps prevent Sybil attacks.
Transaction quantity limit:The airdrop project party can limit the number of transactions that can be made by each address. This can prevent malicious users from obtaining too many tokens by making a large number of transactions.
Holding time limit:The airdrop project party can require that the address holding the token must hold it for a certain period of time to obtain the airdropped tokens. This can prevent malicious users from quickly buying and selling tokens to obtain too many tokens.
Other supporting references:
Social media activity:Registration time, frequency of speaking, quality of speaking (likes and retweets), fans, attention, avatars, profiles, etc. IP address device number: the number of addresses logged in with the same IP/device, the frequency of IP changes at the same address, etc.

What should we pay attention to when participating in airdrops?
Finally, Beosin has also noticed everyone's enthusiasm for airdrops. As a security company, it is necessary for us to make the following reminders for everyone.
1 Understand the official information source of the project: Before participating in the airdrop, you should go to the project's official website and social media page to check the relevant information, including the specific details and rules of the airdrop plan, as well as the contract address of the airdrop token.
2 Do not disclose personal information and wallet addresses easily: Some airdrop projects may require participants to provide personal information and wallet addresses, but you should pay attention to protecting personal privacy and security, and do not disclose sensitive information to unidentified websites and projects.
3 Pay attention to risk warnings and precautions: Before participating in the airdrop, be sure to carefully read the risk warnings and precautions issued by the project party, understand the relevant risks and precautions, and ensure that you have sufficient risk tolerance.
Original link
Welcome to join the official BlockBeats community:
Telegram Subscription Group: https://t.me/theblockbeats
Telegram Discussion Group: https://t.me/BlockBeats_App
Official Twitter Account: https://twitter.com/BlockBeatsAsia
 Forum
Forum OPRR
OPRR Finance
Finance
 Specials
Specials
 On-chain Eco
On-chain Eco
 Entry
Entry
 Podcasts
Podcasts
 Data
Data


 Summarized by AI
Summarized by AI







