A long article explaining the technical principles and development prospects of SSV Network
Original author: Crypto KOL Poopman
Original translation: 0x711, Logicrw, BlockBeats
In early September, Ethereum LSD protocols such as RocketPool, StakeWise, and Stader Labs initiated a joint commitment to limit their market share to no more than 22% of the total staked amount, aiming to address the increasing centralization of the Ethereum staking market. However, the market leader Lido Finance, which accounts for 32% of the market share, did not make a statement on this, sparking controversy in the community. In response, Crypto KOL Poopman posted on his social platform that Distributed Verification Node Technology (DVT) plays an important role in preventing single points of failure and achieving decentralization, and conducted an in-depth analysis of the related protocol SSV Network.
BlockBeats sorted out and translated this as follows.
Background
After the Ethereum merger, the consensus mechanism has transitioned from PoW to PoS. At the same time, PoS has accelerated the growth of staking solutions such as Lido, and also accelerated the risk of protocol centralization (about 33% market share).
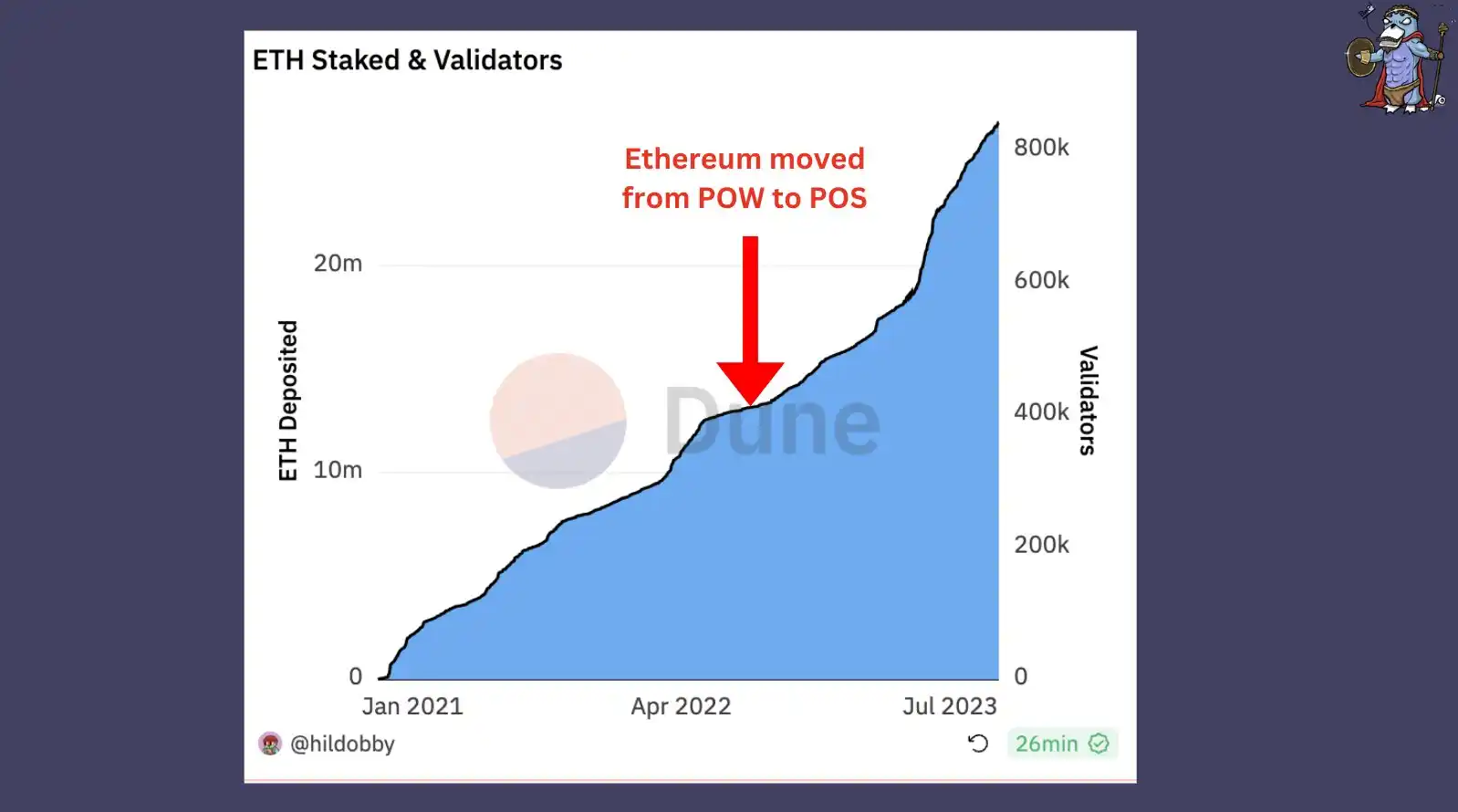
DVT stands for Distributed Validator Technology. This technology distributes the private key of the validator across multiple computers to prevent single point failures, etc. In simple terms, DVT can be regarded as a solution similar to multi-signature.
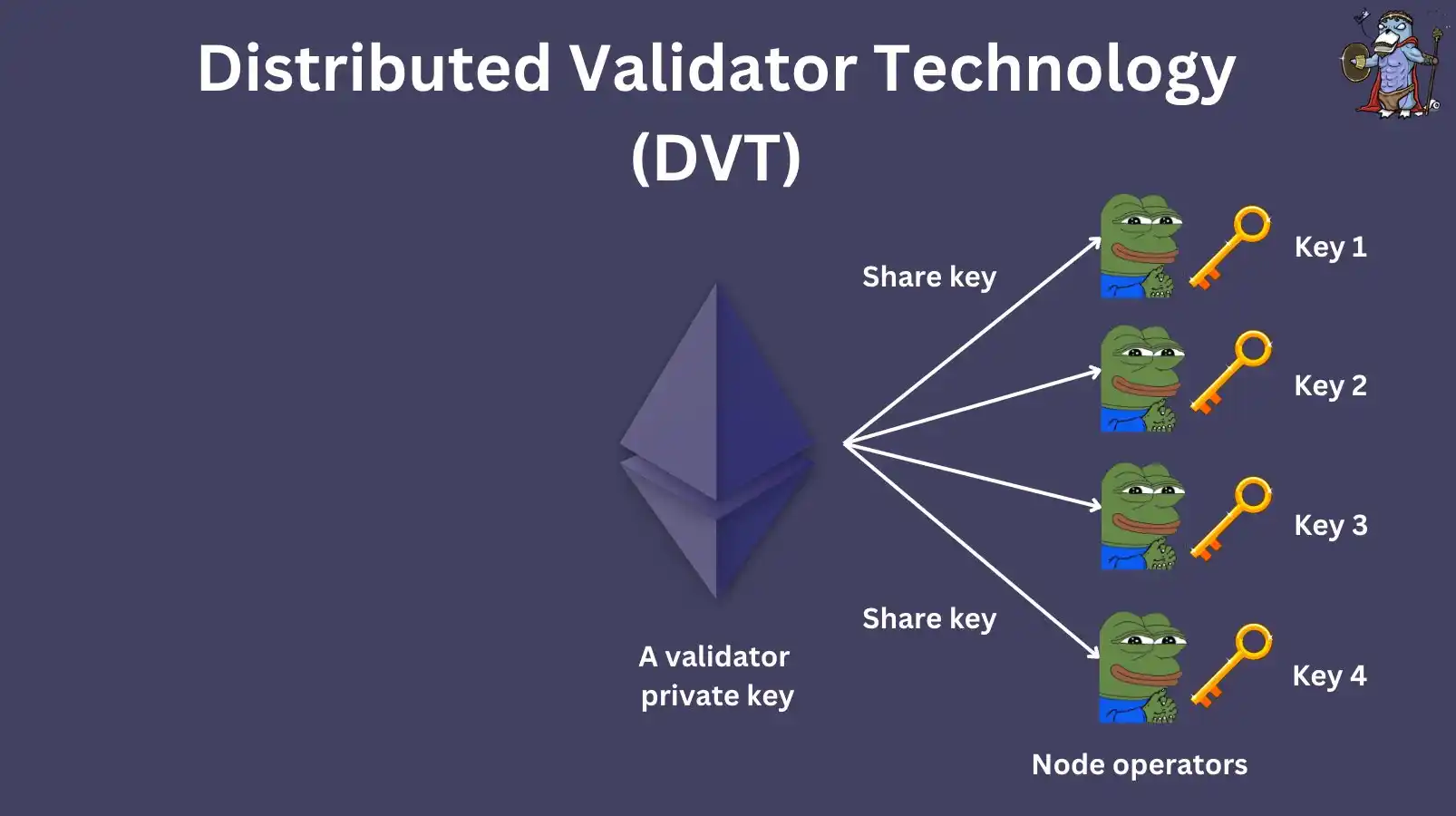
Here we need to explain the concept of validator node key. After POS, the validator node key was introduced. This key is responsible for signing on-chain operations, such as block proposals and proofs. However, the key must be kept in a hot wallet.
How DVT technology works
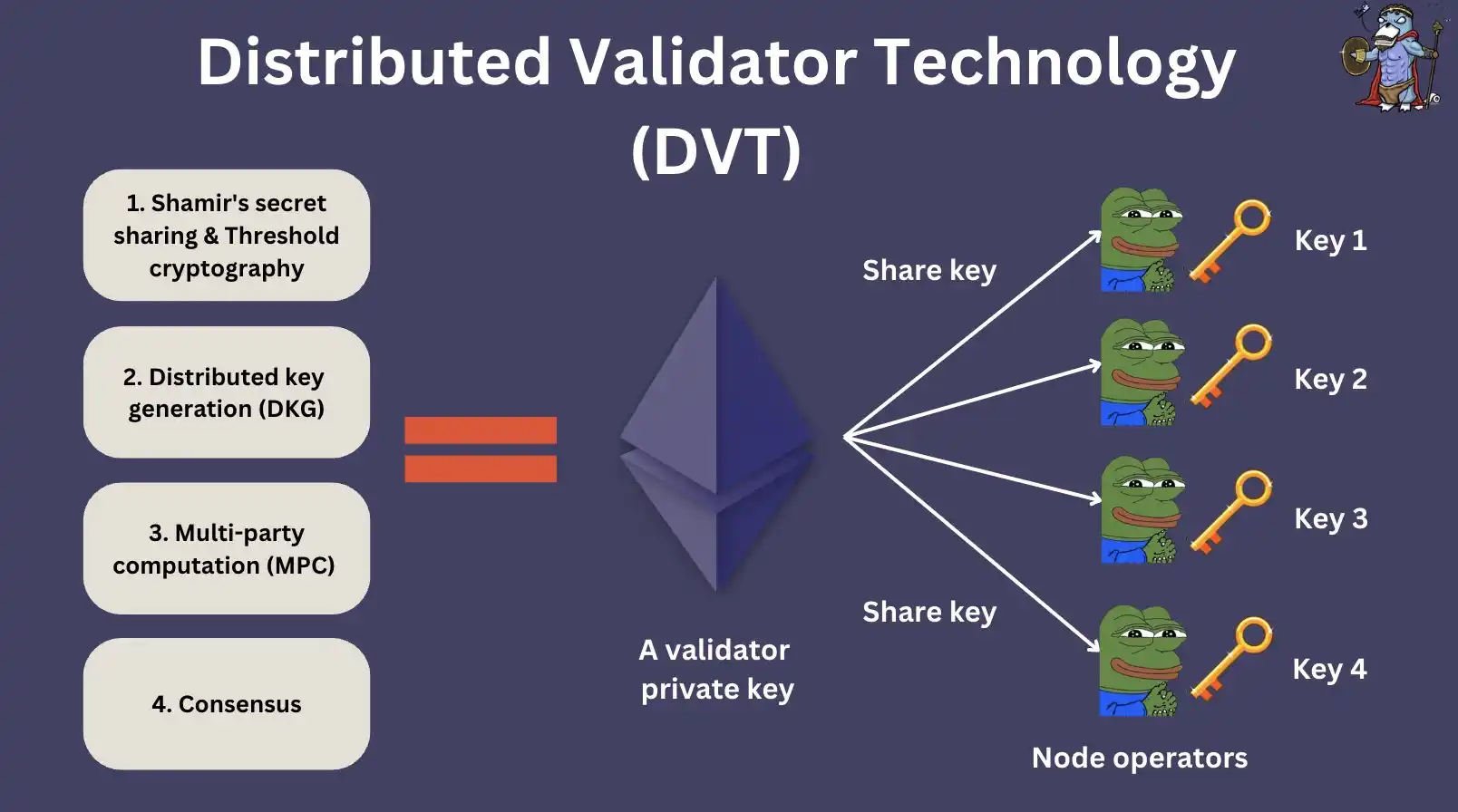
To understand how it works, we first need to understand the 4 pillars of DVT:
1. Shamir's Secret Sharing and Threshold Cryptography;
2. Distributed Key Generation (DKG);
3.MPC;
4. Consensus.
Shamir's Secret Sharing
Imagine a graph, assuming an encrypted message is on the Y axis, and a private key is split into 3 parts and sent to nodes A, B, and C. To decrypt the message, at least 2 parts are required to connect the wires.
This is called ⅔ Shamir's Secret Sharing. In simple terms, Shamir's Secret Sharing is an algorithm that divides a private key among multiple nodes. Each node holds only a small portion of the key, and no single node can sign a message unless a voting threshold (such as 3/4 or 5/7) is reached.
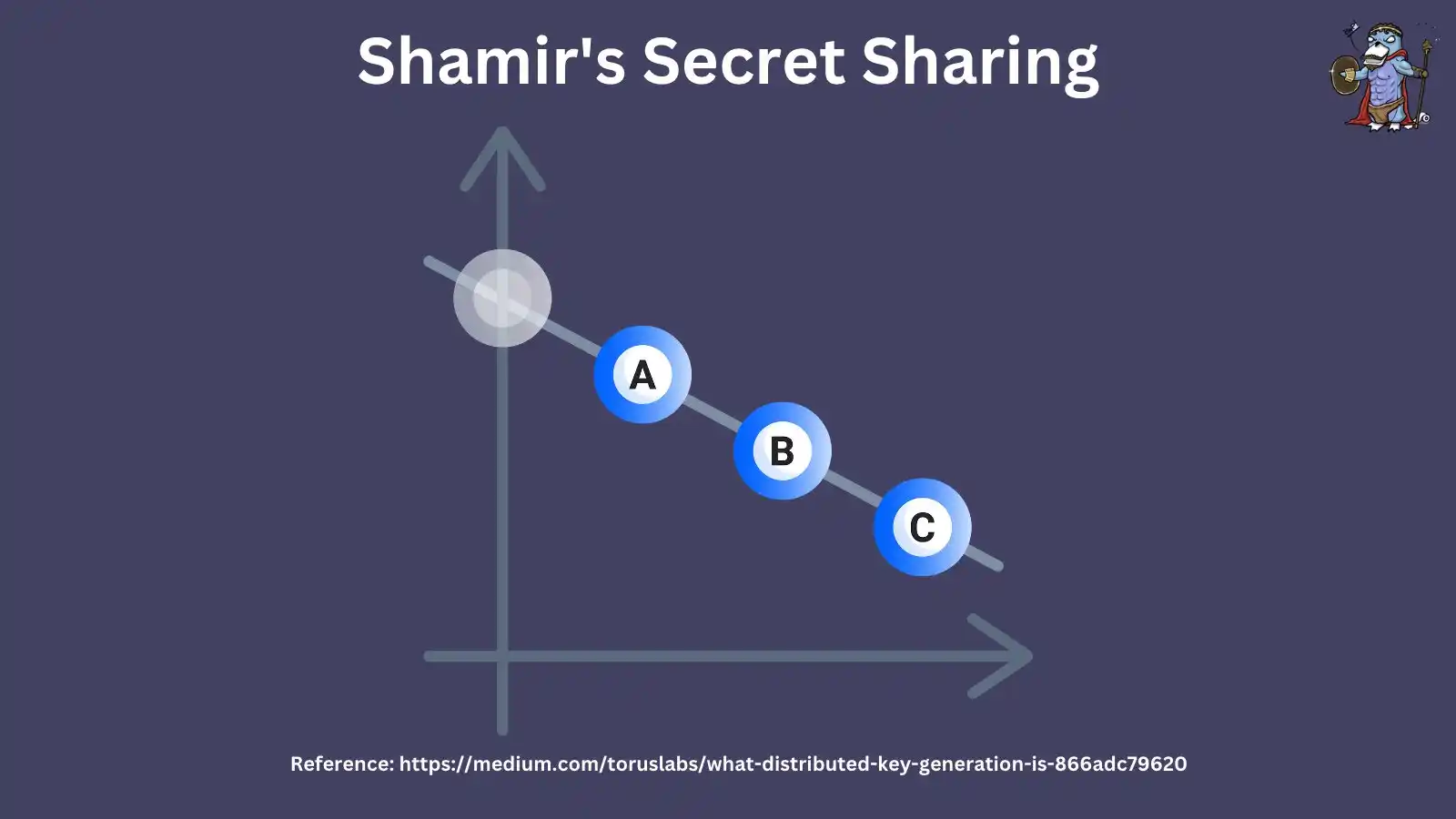
In addition, POS uses BLS signatures, which allow multiple signatures to be aggregated into a single signature. Therefore, when a node signs a transaction, the BLS signature combines all signatures into a signature that can represent the private key of the verification node.
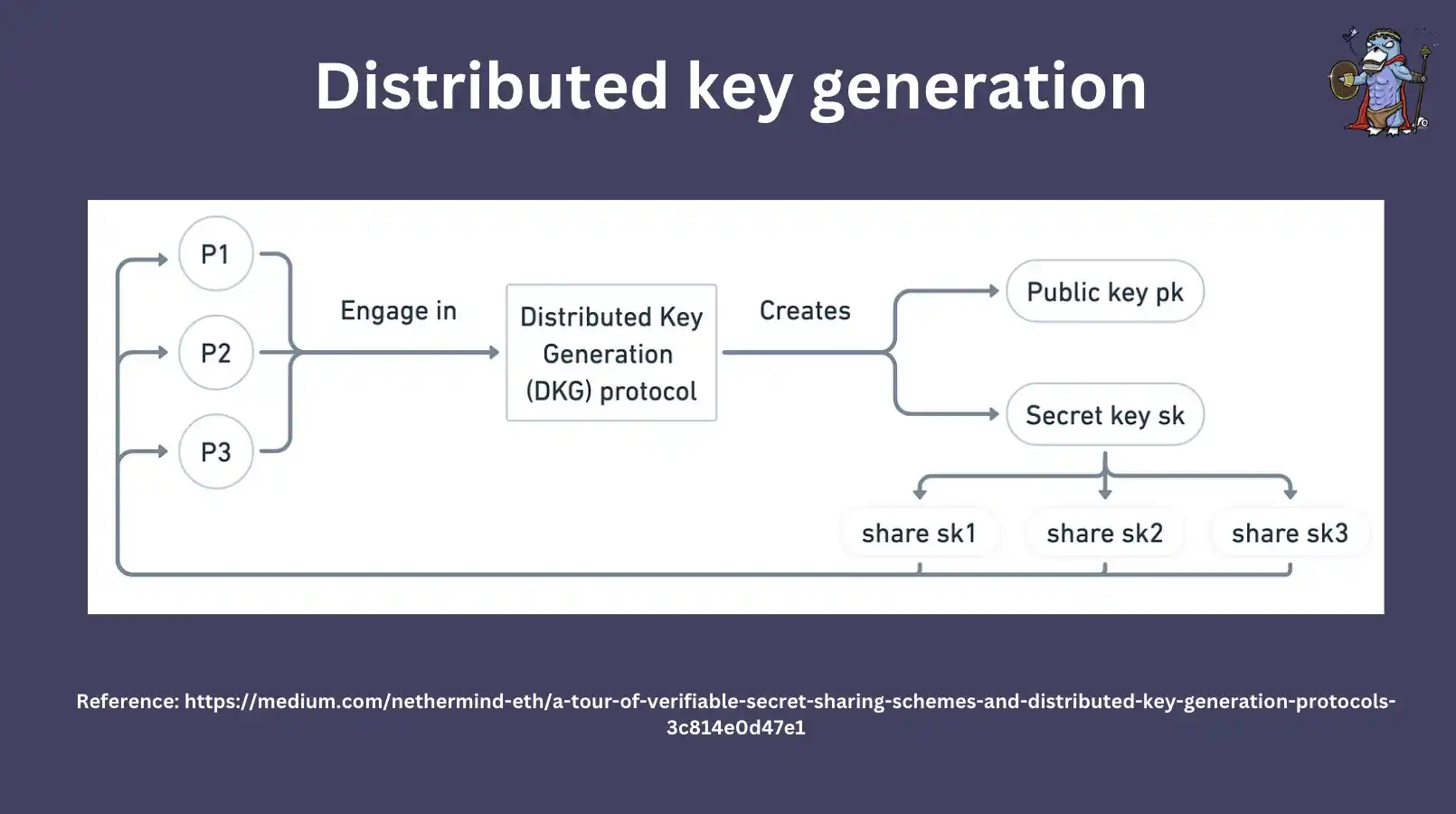
Distributed Key Generation (DKG)
However, the reality is that no party should know the private key of this verification node, because this is very insecure for the verifier. In this case, DKG tries to solve this problem in the following way:
Each participant makes a secret share;
All these shares are then added together to get the final result.
Therefore, DKG is a process of creating a key share and distributing it to each node. This process requires each participant to calculate the key and provide "randomness" to it so that no single party can learn the user's private key.
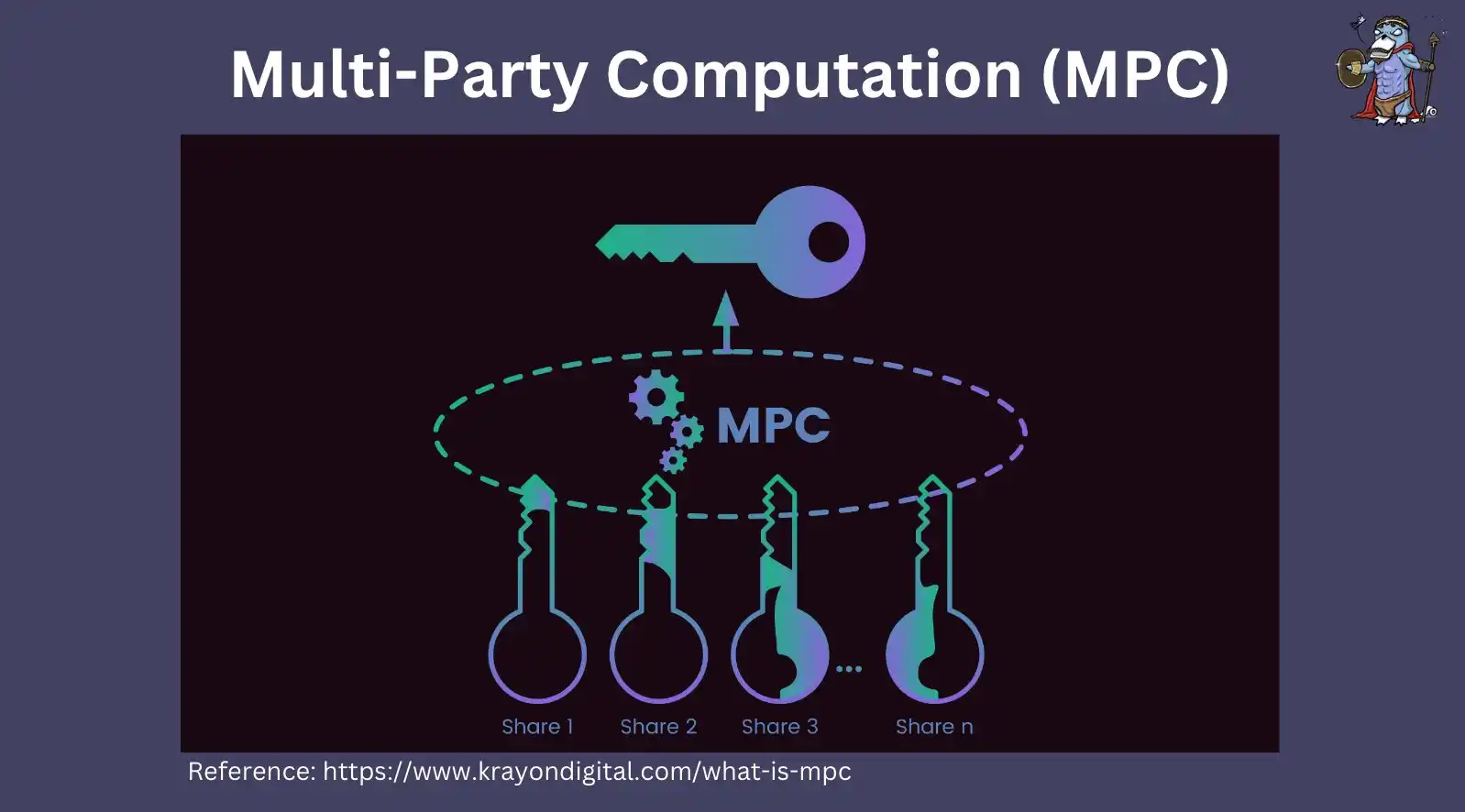
Multi-party computation (MPC)
MPC is an important pillar of DVT. MPC allows operators to sign messages using only their secret share without having to reconstruct the full private key on any single device. This helps reduce the risk of private key centralization.
Consensus Mechanism
In order to reach a consensus on a block between nodes, the IBFT algorithm selects a node as a block proposer and shares the block with other nodes. If consensus is reached, meaning that approximately 66% of the nodes agree that the block is valid, the block is proposed for packaging.
However, if the block proposer goes offline due to hardware/software issues in DVT, the IBFT consensus will select another DVT node as the block proposer within 12 seconds, and the fault tolerance mechanism will take effect. (This guarantees the robustness of the blockchain to a certain extent.)
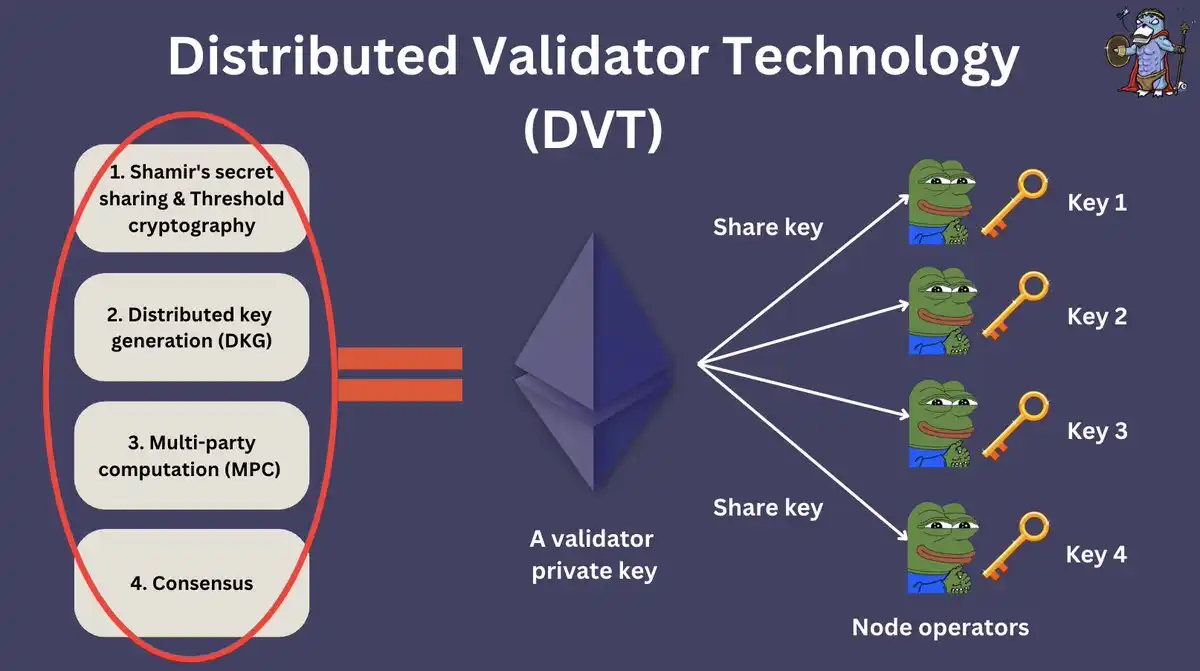
Brief Summary of DVT
In short, the following four technologies form the basis of DVT:
1. Shamir's Secret Sharing and Threshold Cryptography
2. DKG
3. MPC
4. Consensus
Now that DVT is understood, let's discuss SSV Network.
What is SSV Network?
SSV stands for Secret Shared Validators, recently known as DVT.
The concept of SSV originated from a research paper in collaboration with members of the Ethereum Foundation, which aims to decentralize the task of validators to a group of nodes.
How does SSV Network work?
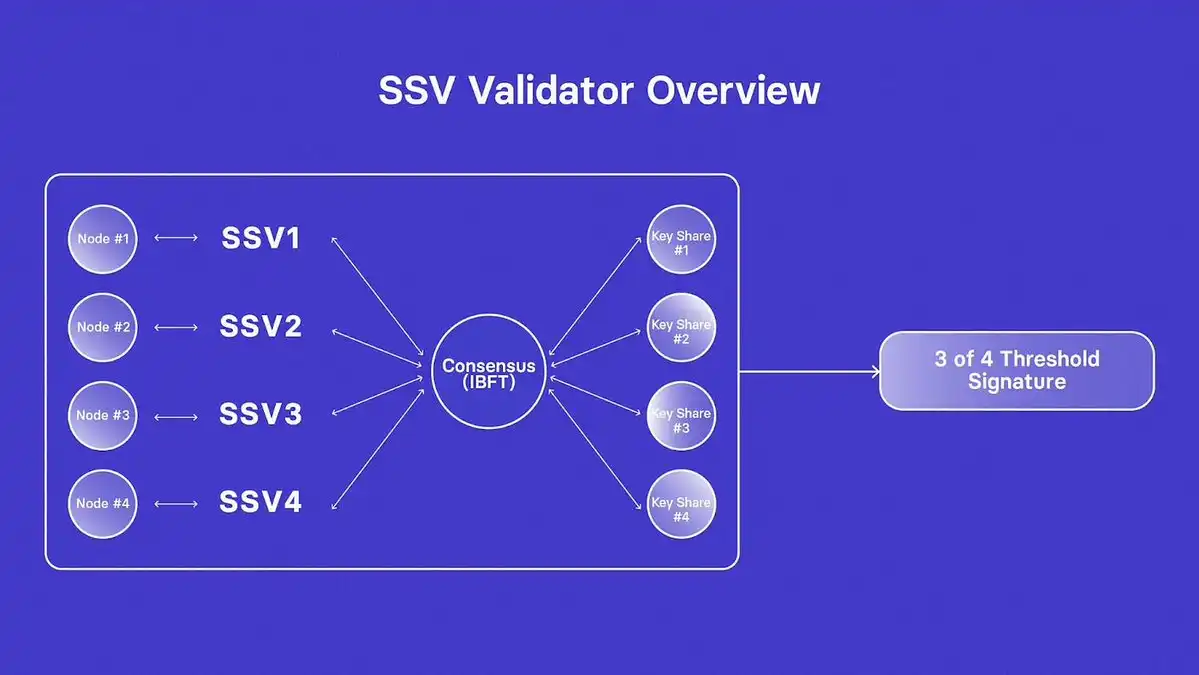
SSV = DVT
SSV distributes the private keys (or shares) of validators to a group of nodes, ensuring:
There is no centralization of keys
A node does not need to trust another node to operate
In addition, SSV has a token and a P2P market.
Use of SSV Tokens
Since the SSV network provides higher security and decentralized services, users must pay SSV fees to the network and operators for incentives.
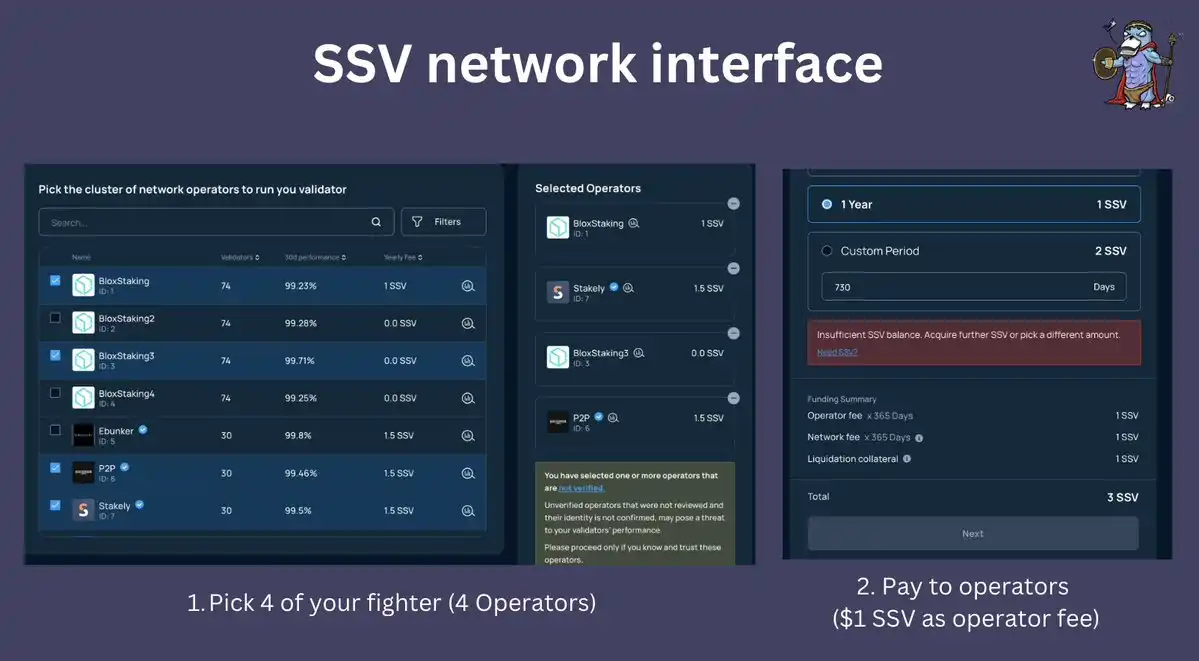
There are two main players in the SSV network: stakers and operators.
Stakers can choose 4 operators from the list, then deposit SSV with these operators and earn ETH directly on the chain according to the term they choose (e.g. 1 year, 6 months).
Each operator can set its own fees and compete with other operators in the P2P market.
More importantly, operators do not hold stakers’ ETH assets or rewards, as their role is simply to maintain and operate validators on behalf of stakers. However, both operators and the network charge operating fees and network fees to users who use the SSV network.
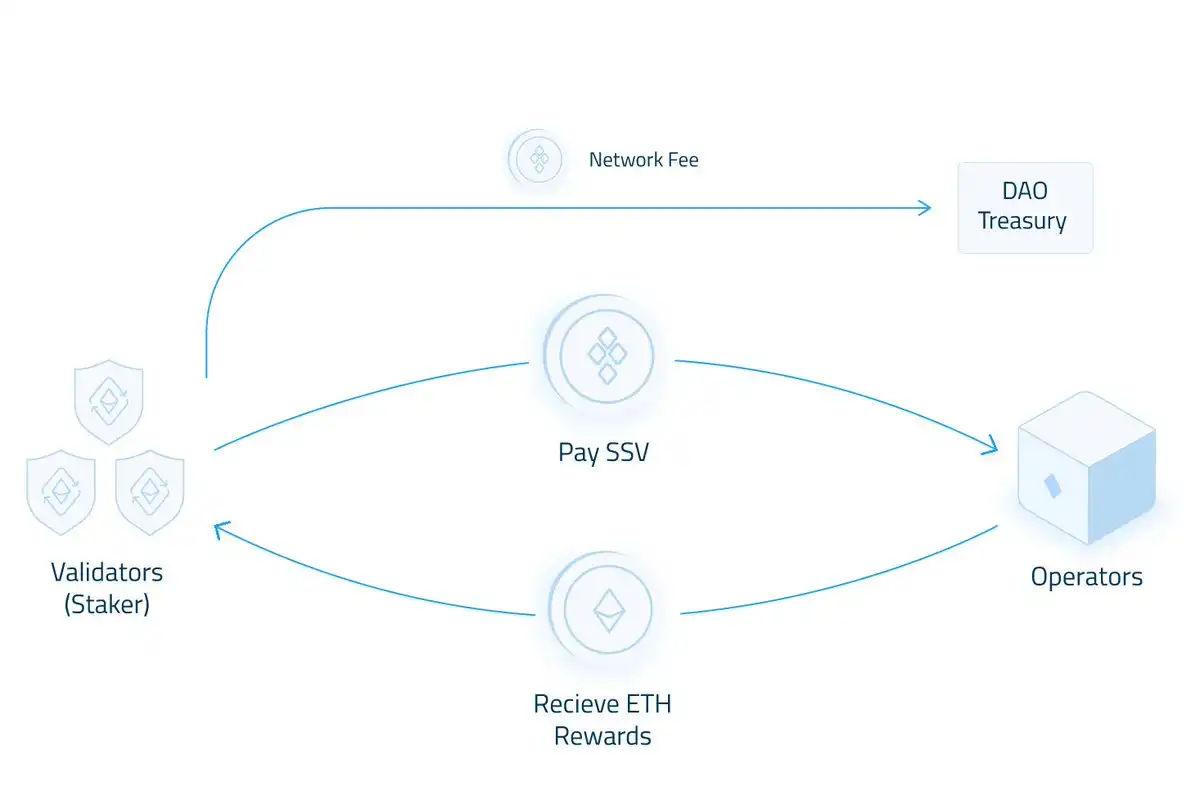
Network fees are a fixed cost per validator designed by the DAO and flow directly into the DAO Treasury (0xb35096b074fdb9bbac63e3adae0bbde512b2e6b6). Fees are deducted from stakers’ SSV balances over time, which have accumulated about $10 million in TVL so far.
SSV DAO
SSV token holders can participate in the governance of SSV DAO and make the following decisions:
Design and adjust network fees
Operator scoring (scoring operators based on their performance)
Development and decision-making of any protocol
SSV feasibility insights
First, the SSV Network is expected to see more adoption. This will lead to more stakers depositing SSV with operators for greater security and decentralized services, resulting in less circulating supply on the market.
In this case, the most intuitive action is to trade SSV on the secondary market.
Alternatively, you can provide liquidity for the SSV-ETH pair on Uniswap (0.3% fee tier) and earn about 64% APR/$1.76 per day per $1,000 liquidity position.

On the other hand, one can also consider running a node in the SSV network and earning SSV as a service fee. The more key shares managed, the more SSV earned.
However, operators need to be aware that the appreciation of SSV does not necessarily lead to higher revenue. In fact, when the price of SSV increases, operators usually lower fees to attract more stakers.
Similarly, when the price of SSV decreases, they also raise fees. This fee dynamic is also affected by how many stakers and operators there are in the market.
Welcome to join the official BlockBeats community:
Telegram Subscription Group: https://t.me/theblockbeats
Telegram Discussion Group: https://t.me/BlockBeats_App
Official Twitter Account: https://twitter.com/BlockBeatsAsia
 Forum
Forum OPRR
OPRR Finance
Finance
 Specials
Specials
 On-chain Eco
On-chain Eco
 Entry
Entry
 Podcasts
Podcasts
 Data
Data


 Summarized by AI
Summarized by AI