Introduction
In today’s digital communications, the sender and receiver of information are very Few are directly contacted. When you communicate with a friend, the exchange of information is private on the surface, but the relevant information is recorded and stored on a central server.
You may not want the server delivering the message to read private messages. In this case, end-to-end encryption (abbreviated as "E2EE") is a feasible solution.
End-to-end encryption is a technical means of encrypting the communication between the receiver and the sender,onlyOnly both parties can decrypt the data. The origins of end-to-end encryption can be traced back to the 1990s, when Phil Zimmerman introduced "Pretty Good Privacy" (known as PGP).
Before introducing why E2EE is used and how it works, let’s first understand how unencrypted messages work.
How unencrypted messages work
This section explains how regular smartphone messaging platforms work. Start by installing the app and creating an account, which allows you to communicate with other users performing the same actions. You edit a message and enter your friend's username, posting it to a central server. The server forwards the message to your friend and successfully delivers the message to the destination.

User A communicates with B. The two must pass data through the server (S) to establish contact.
You can It's called the "client-server model". The client (your phone) performs very few operations and all the heavy computational processing is done by the server. Therefore, the service provider acts as an intermediary between you and the recipient.
In most cases, A <> S and S <> B has been encrypted. An example is Transport Layer Security (TLS), which is widely used to protect connections between clients and servers.
TLS and similar security solutions prevent interception of messages as they pass from the client to the server. While these measures prevent outsiders from accessing the data, the central server is responsible for encrypting the information and therefore still has access to read the data. If A's data is encrypted using B's encryption key, the server cannot read or access it.
If E2EE is not used, the server will store this information in the database together with millions of other pieces of information. Large-scale data breaches have repeatedly proven that this vulnerable mechanism can bring disaster to users.
How end-to-end encryption works h2>
End-to-end encryption ensures that no one, not even the server, has access to your communications. The communication content can be in any form such as plain text, email, file, video call, etc.
Data is encrypted (in theory) in applications such as Whatsapp, Signal or Google Duo, and only the sender and intended recipient can Decrypt. In an end-to-end encryption scheme, you start the process using a method called Key exchange.
What is DI Phi-Hellman key exchange?
Diffie-Hellman key exchange is the work of cryptographers Whitfield Diffie, Martin Herman and Co-conceived by Ralf Merkel. This powerful technology helps parties generate and share secrets in potentially dangerous environments.
In other words, even if the key is created in an insecure forum (even in the presence of bystanders), it will not affect the confidentiality of future communications. sex. This mechanism is extremely valuable in the information age, allowing two parties to communicate without physically exchanging keys.
The exchange itself involves a large number of numbers and wonderful cryptographic techniques, which will not be introduced in detail in this article. Instead, let's use the analogy of common paint colors: Suppose Alice and Bob book rooms at opposite ends of a hotel corridor, and they want to share a specific color of paint, but don't want to reveal the specific color.
Unfortunately, the floors are filled with spies. Suppose Alice and Bob cannot enter each other's rooms and can only communicate and interact in the corridor. The two were in the hallway and decided to paint the room yellow. They split the yellow paint they got into two and went back to their rooms.
In the room, they mix another secret color that no one knows about. Alice used dark blue, and Bob used dark red. The key is that the spy doesn't have access to the secret colors they used, but can see the resulting mixture because Alice and Bob now leave the room with a mixture of blue-yellow and red-yellow.
The two publicly exchanged the above mixture. It didn't matter if the spies saw it, they had no idea what the dark tones were added to. This is just an analogy, real mathematical systems are very complex and guessing the secret "color" is no easy task.
Alice and Bob get each other's mixture and return to the room, then add their secret colors to the mixture.
Alice mixes the secret color "dark blue" with Bob's red and yellow to form red-yellow -Blue mixture
Bob mixes the secret color "dark red" with Alice's blue-yellow to form a blue-yellow-red mixture.
Both combinations are the same color and have the same appearance. Alice and Bob successfully create a unique color unknown to the spy.
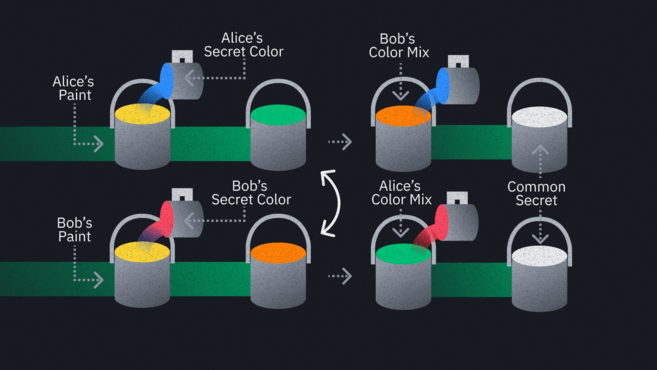
This is how we create shared secrets in an open environment. The difference is that instead of dealing with hallways and paint, we're dealing with insecure channels, public and private keys.
Information exchange
Once other parties have their shared secret, they can use it as the basis for a symmetric encryption scheme. Current mainstream encryption solutions usually use multiple technologies to improve security, but these solutions are all "made behind closed doors" that are divorced from actual needs, and therefore have little effect. Once connected to a friend via the E2EE app, encryption and decryption can only be done within your device, unless there is a major software vulnerability.
Hackers, service providers, or law enforcement officials are all included. If the service got true end-to-end encryption, any messages intercepted would be garbled.
➟ Want to start a digital currency journey? Buy Bitcoin on Binance today!
Advantages and disadvantages of end-to-end encryptionDisadvantages of end-to-end encryption
End-to-end encryption actually has only one disadvantage, and whether it counts as a disadvantage varies from person to person. In the eyes of some, the value proposition of E2EE itself is problematic, since no one can access your messages without the corresponding key.
Opponents believe that this creates an opportunity for criminals because they know that governments and technology companies cannot decrypt E2EE. communication. There is no need for law-abiding individuals to keep messages and calls confidential. Many politicians agree. They are calling for legislation that would allow regulators to intervene in the public's communications when necessary. Of course, this defeats the purpose of using end-to-end encryption in the first place.
It is worth noting that applications using E2EE also face security risks. When two devices communicate, the messages may be mixed up, but they will appear normally at their respective endpoints (i.e. laptops or smartphones on both ends). This in itself is not considered a disadvantage of end-to-end encryption, but it is something to be aware of.

The message appears in plain text before and after decryption.
E2EE technical guarantee No one can read your data while in transit, but other threats remain:
Device can be stolen: If there is no PIN or if an attacker bypasses PIN protection, they can view your messages.
Device may be compromised: Your computer may have malware installed that monitors your messages before and after they are sent.
Another major risk is that criminals may forcefully intervene in the communication between the two parties through man-in-the-middle attacks. This usually happens at the beginning of communication. If a key exchange is in progress, it will be difficult to be certain that the person you are exchanging keys with is actually the friend. You may have established a secret connection with an attacker without knowing it. After the attacker receives your message and has the decryption key, he can deceive your friends in the same way and intercept the message to peek or tamper with the relevant content as needed.
In order to solve this problem, many Apps integrate corresponding security code functions, which may be in the form of a string of numbers or a QR code , you can share it with your contacts through a secure channel (offline recommended). If the numbers match, you're sure a third party isn't listening in on your communications.
Advantages of end-to-end encryption
In settings without any of the above vulnerabilities, E2EE undoubtedly improves confidentiality and security Effective Ways. Similar to onion routing, E2EE has won over privacy advocates around the world. This technology can be easily embedded into existing applications to serve all mobile phone users.
E2EE is more than just a mechanism for dealing with criminals and whistleblowers. It turns out that seemingly impregnable companies are also vulnerable to cyberattacks, resulting in the leakage of unencrypted user information to bad actors. Exposure of user data such as sensitive communications, identity documents, etc. may cause a major blow to personal lives.
If a company using the E2EE mechanism is compromised, as long as the encryption scheme is solid and reliable, the hacker will not be able to steal any meaningful information . In the worst case, they only have metadata. From a privacy perspective, this risk cannot be ignored, but the security of encrypted messages has indeed been improved.
Summary
In addition to the applications mentioned above, various free E2EE tools have been launched and promoted. Apple and Google have customized iMessage and Duo for iOS and Android operating systems respectively, and software focusing on privacy and security is also constantly being released.
We must reiterate that end-to-end encryption is not a universal shield against all cyberattacks. However, with some simple settings and operations, this technology can significantly reduce the risk of information leakage and create a secure network communication environment. In addition to Tor, VPN, and cryptocurrencies, the E2EE communication program is also a powerful tool for protecting digital privacy.
 Forum
Forum OPRR
OPRR Finance
Finance
 Specials
Specials
 On-chain Eco
On-chain Eco
 Entry
Entry
 Podcasts
Podcasts
 Data
Data
