Directory
- Introduction
- What is a private key?
- What is a hardware wallet?
- Why should you use a hardware wallet?
- Limitations of Hardware Wallets
- Hardware Wallet Reviews 2020
- Ledger Nano S
- Ledger Nano X
- Trezor One
- Trezor Model T
- Cobo Vault
- CoolWallet S
- SafePal
- KeepKey
- Summary
Introduction
For encryption Currency, good storage is crucial. The cryptocurrency world is full of dangers – people with malicious intentions are everywhere, and there are endless ways for them to steal user funds. Therefore, developing a strategy to protect your coins should be your first priority.
There are many ways to store your cryptocurrency, each of which comes with trade-offs in terms of security and usability. Most of the time, newbies use exchanges. These platforms have given many people the opportunity to get into cryptocurrencies for the first time and allow users to store funds in online wallets. But technically speaking, users do not control their own tokens. If an exchange is hacked or goes offline, users may not be able to recover their funds.
Users may not see the need to move their cryptocurrencies off exchanges. They may lack relevant skills and may even believe that hosted solutions are more secure. After all, if users keep it on their own, making a mistake could result in a loss of funds.
Taking control of your own cryptocurrency can be an intimidating idea. But from a security perspective, hardware wallets are highly reliable. In this article, we will explain what a hardware wallet is, how a hardware wallet works, and why you should use a hardware wallet.
What is a private key?
Your private key is your passport into the cryptocurrency ecosystem. In many ways, it's like a real-life key - with this information, you can unlock your funds and spend them. Once someone gets their hands on this key, they can steal your cryptocurrency. If you lose your private keys, you have no access to your tokens – there is no forget password button in a decentralized environment, and there are no banks to help you cancel fraudulent transactions.
The most basic requirement is that you must keep your private key private and secure. They are extremely valuable to cryptocurrency users. Predictably, hackers and scammers will constantly try to steal them – using phishing techniques or malware to steal tokens from users.
Storing keys is very simple, they are just a string of numbers and letters that can be written on paper or stored in a safe. However, to use a private key to transfer funds, the private key must be stored on a device that proves you are eligible to spend the coins.
What is a hardware wallet?
Hardware wallets are devices designed to securely store private keys. It is considered more secure than a desktop or smartphone wallet, mainly because it is not connected to the internet under any circumstances. These features significantly reduce the attack vectors that malicious parties can exploit because they cannot remotely tamper with the device.
A good hardware wallet ensures that the private keys never leave the device. They are usually stored in a special location in the device and cannot be removed.
Since hardware wallets are always offline, they must be used with another machine. The way they are built means they can be plugged into an infected PC or smartphone without the risk of leaking private keys. They can then interact with the software, allowing users to view their balances or make transactions.
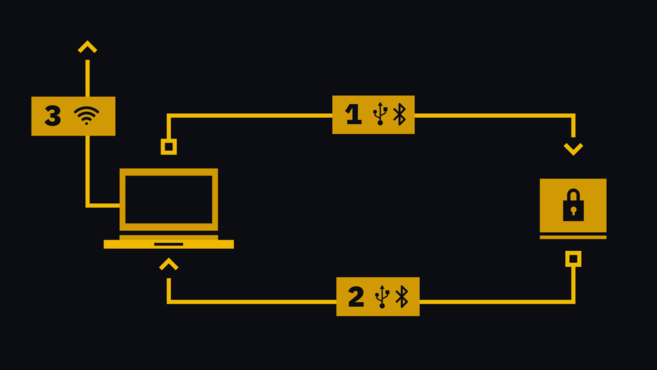
Once the user creates a transaction, the hardware wallet will send the transaction to the hardware wallet (1 in the image below). Note that the transaction is not completed at this point: it needs to be signed by the private key in the device. The hardware device will pop up a prompt asking the user to confirm that the amount and address are accurate. The transaction is then signed and sent back to the software (2), which broadcasts it to the cryptocurrency’s network (3).
Why should you use a hardware wallet?
Storing private keys in a wallet on an internet-connected computer or smartphone leaves users’ funds vulnerable to a variety of attacks. Malware can detect crypto-related activity on these devices and drain users of their funds.
A hardware wallet is like an unbreakable vault with a small slot. When a user wishes to create a transaction that is accepted by the network, it is pushed into this slot. Imagine that on the other side of the slot there is an elf performing some cryptographic magic, signing transactions. The elf will never leave the vault - since the vault has no door, and the elf cannot pass through the slot. All it can do is accept transactions and send transactions.
Even if your hardware wallet accidentally falls into the wrong hands, you have extra protection in the form of a PIN code. If you enter the wrong password a certain number of times, the device will usually reset.
Funds that are not actively used, such as those that have not been spent, pledged, loaned, or traded, should be kept in cold storage. To do this, hardware wallets provide users with a convenient method that even those with limited technical knowledge can use.
Hardware wallets must be backed up to prevent loss, theft or destruction. Upon initialization, users are typically prompted to record their mnemonic phrase, which is a set of words that can be used to recover funds on the new device. This would make their tokens available to anyone and therefore should be considered valuable. Users are advised to write them on paper (or etch them on metal) and keep them in a private and secure location.
Limitations of Hardware Wallets
Like other forms of storage, hardware wallets have their own pros and cons. While they are one of the safest mediums to hold coins, there are still some limitations. They strike a balance between security and usability. Smartphone/software wallets are convenient and easy to use, while hardware wallets can be cumbersome to operate since they require the use of two devices at the same time to actually send funds.
Having said that, hardware wallets are not foolproof. Users may be forced to unlock their wallets for their abusers if they face physical threats, but there are other factors at play. A sophisticated malicious party could potentially exploit the device if they gained physical access to it.
However, so far, no hacker has successfully obtained the private key from the hardware device in a real scenario. Once a vulnerability is reported, manufacturers typically patch it quickly. That’s not to say that stealing private keys from hardware wallets can’t happen – researchers have shown that even the most popular wallets can be compromised.
Supply chain attacks can also effectively compromise the security of hardware wallet devices. This can happen if a malicious actor obtains the wallet before it is delivered to the user. This allows them to tamper with wallets, weaken wallet security, and steal funds after users deposit their coins.
Another limitation is that the hardware wallet needs to be kept by you personally. Many people consider this an advantage because your funds are not managed by a third party. But it also means that if something goes wrong, there's no support.
Hardware Wallet Reviews 2020
Binance Academy has been reviewing the most popular hardware wallets on the market Conduct a series of reviews.
Ledger Nano S
The Ledger Nano S is undoubtedly one of the most popular hardware wallets today , both long-term holders and high-frequency traders consider it a must-have option. Read the full Ledger Nano S 2020 review.
Ledger Nano X
As the successor of Ledger Nano S, Nano Feature upgrades, including wireless capabilities and support for more cryptocurrencies. Read the full Ledger Nano X 2020 review.
Trezor One
The product that spawned the hardware wallet industry is still going strong. Affordable yet powerful, the Trezor One remains the gold standard for many cryptocurrency holders. Read the full Trezor One 2020 review.
Trezor Model T
An evolution of the Trezor One. Although more expensive, it comes with a touch screen, supports more coins, and is SD card compatible for easy future upgrades. Read the full Trezor Model T 2020 review.
Cobo Vault
This is a wallet designed for the apocalypse. The sealed touchscreen device is housed in a rugged metal casing for those who value safety. Read the full Cobo Vault 2020 review.
CoolWallet S
CoolWallet S is only the size of a credit card, and it is definitely a product that people can’t put down. equipment. Although it still needs improvement in terms of UI/UX, it can still attract users who are looking for something different. Read the full CoolWallet S 2020 review.
SafePal
For its price, SafePal implements some very interesting security features, making it as safe as possible Reduced interaction with other devices. Read the full SafePal S1 2020 review.
KeepKey
A stylish device integrated with native ShapeShift. However, users need to register to use its full functionality. Read the full KeepKey 2020 review
Did we miss your favorite device? Feel free to tweet us @BinanceAcademy!
Summary
The limitations of hardware wallets do not overshadow their advantages. As storage solutions evolve, the security of hardware wallets remains difficult to match. There is no substitute for cold storage and it removes a lot of the risk of self-custodying your funds.
When looking for a hardware wallet, users should have a thorough understanding of the wallets available to choose from. There are a variety of devices on the market, each with different features, supported cryptocurrencies, and learning curves.


 Forum
Forum Finance
Finance
 Specials
Specials
 On-chain Eco
On-chain Eco
 Entry
Entry
 Podcasts
Podcasts
 Activities
Activities
 OPRR
OPRR
